Featured image for how to access a nvr on a different subnet
Image source: s3.amazonaws.com
Accessing a NVR on a different subnet in 2026 requires proper routing and firewall configuration to enable secure cross-subnet communication. Ensure your network uses static routes or VLANs to bridge subnets, and verify that the NVR’s IP is reachable through configured port forwarding or a site-to-site VPN. Always prioritize encryption and access controls to protect video data during remote access.
Key Takeaways
- Verify network compatibility: Ensure subnets can communicate via routing or VLANs.
- Configure static routes: Set up routes on routers to bridge subnet gaps.
- Use a VPN: Securely connect to the remote subnet with encrypted tunnels.
- Update NVR firmware: Ensure latest security and remote access features are active.
- Open firewall ports: Allow necessary traffic while minimizing exposure risks.
- Leverage cloud services: Use manufacturer platforms for seamless cross-subnet access.
📑 Table of Contents
- The Challenge of Accessing a NVR on a Different Subnet in 2026
- Understanding Subnets and NVR Network Architecture
- Method 1: Configuring Static Routes for Inter-Subnet Access
- Method 2: Using Port Forwarding and NAT Traversal
- Method 3: Deploying a Site-to-Site VPN for Secure Access
- Advanced Techniques: VLANs, Cloud Integration, and Zero Trust
- Comparative Analysis: Choosing the Right Method for Your Needs
- Conclusion: Mastering Cross-Subnet NVR Access in 2026
The Challenge of Accessing a NVR on a Different Subnet in 2026
In the rapidly evolving landscape of security technology, Network Video Recorders (NVRs) have become the backbone of modern surveillance systems. As businesses and homes grow increasingly interconnected across multiple networks, the need to access a NVR from a different subnet has never been more critical. Whether you’re a security professional managing a multi-site enterprise, a homeowner with a remote property, or an IT administrator overseeing a complex network infrastructure, understanding how to access a NVR across subnets is essential for maintaining seamless surveillance and operational efficiency.
Imagine this scenario: your primary office is located in New York, but your warehouse operates in Los Angeles. The NVR storing critical footage from both locations is physically located in LA, but your monitoring team works remotely from New York. Without proper configuration, accessing the LA-based NVR from the NY subnet becomes a technical hurdle—leading to delayed incident response, inefficient troubleshooting, and potential security gaps. In 2026, with cloud integration, AI-powered analytics, and hybrid network models becoming standard, mastering cross-subnet NVR access is no longer optional—it’s a necessity. This guide will walk you through the technical principles, practical configurations, and best practices to ensure you can access your NVR securely and efficiently, no matter where your network segments reside.
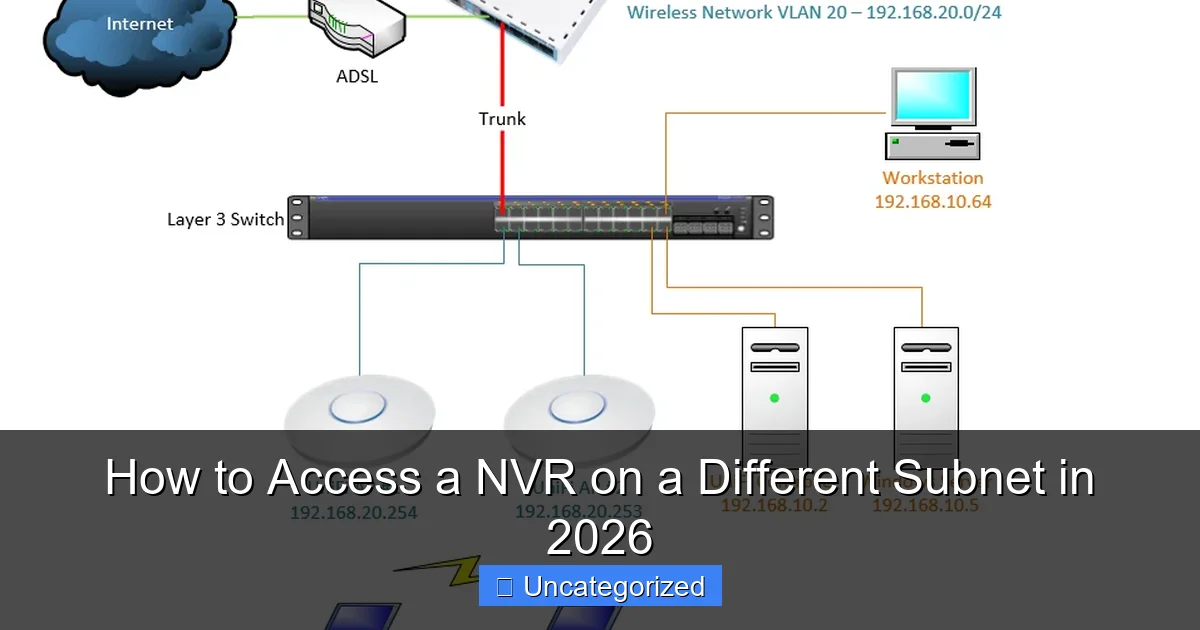
Understanding Subnets and NVR Network Architecture
Before diving into the technical steps, it’s crucial to grasp the foundational concepts of subnets and how they interact with NVR systems. A subnet (short for subnetwork) is a logical division of an IP network that allows devices to communicate within a defined range of IP addresses. Subnets are created using subnet masks, which determine how IP addresses are partitioned into network and host portions. For example, a typical home network might use the 192.168.1.0/24 subnet, allowing up to 254 devices with IPs from 192.168.1.1 to 192.168.1.254.
Visual guide about how to access a nvr on a different subnet
Image source: use-ip.co.uk
Why Subnets Matter for NVR Access
NVRs are designed to operate within a specific subnet, typically communicating with IP cameras, management software, and remote users. When a client (e.g., a monitoring workstation) is on a different subnet than the NVR, direct communication is blocked by default due to routing limitations. Routers, which connect subnets, do not forward broadcast traffic and often restrict inter-subnet communication unless explicitly configured. This is where routing rules, firewall settings, and port forwarding come into play.
- Subnet Isolation: Enhances security by limiting broadcast domains and reducing attack surface.
- Traffic Segmentation: Prevents surveillance traffic from congesting other network segments (e.g., VoIP or data).
- Scalability: Allows large organizations to deploy NVRs across multiple locations without IP conflicts.
Typical NVR Network Topologies
Modern NVR systems can be deployed in various network configurations:
- Single-Subnet Setup: NVR and cameras reside on the same LAN (e.g., 192.168.1.0/24). Easy to manage but not scalable.
- Multi-Subnet Enterprise: NVR in one subnet (e.g., 10.0.1.0/24), cameras in another (10.0.2.0/24), and remote access via a third subnet (e.g., 10.0.3.0/24).
- Hybrid Cloud-Local: NVR on-premise with cloud-based access (e.g., via a VPC in AWS or Azure).
Understanding your network topology is the first step toward enabling cross-subnet NVR access. For instance, a multi-subnet enterprise requires static routing, while a hybrid model may leverage VPNs or cloud gateways.
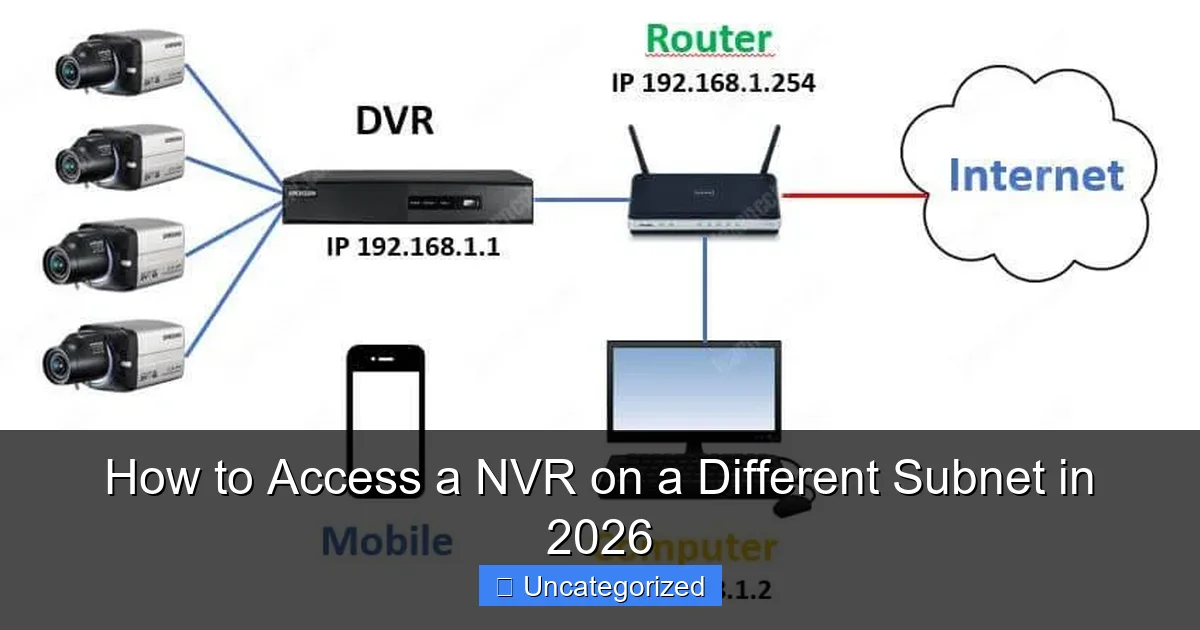
Method 1: Configuring Static Routes for Inter-Subnet Access
Static routing is one of the most reliable and secure methods to enable communication between subnets. It involves manually defining paths in your router’s configuration so that traffic destined for the NVR’s subnet is correctly forwarded. This method is ideal for environments with stable, predictable network layouts—such as office buildings, campuses, or industrial facilities.
Visual guide about how to access a nvr on a different subnet
Image source: learncctv.com
Step-by-Step Static Route Configuration
Let’s assume the following network setup:
- NVR Subnet: 192.168.10.0/24 (NVR IP: 192.168.10.100)
- Remote Access Subnet: 10.0.0.0/24 (Workstation IP: 10.0.0.50)
- Router 1 (NVR Side): 192.168.10.1 (gateway)
- Router 2 (Remote Side): 10.0.0.1 (gateway)
Step 1: Access Router 2 (Remote Side)
- Log into the web interface of Router 2 (e.g., via 10.0.0.1).
- Navigate to Routing > Static Routes (exact path varies by router model).
- Add a new static route:
- Destination Network: 192.168.10.0
- Subnet Mask: 255.255.255.0
- Gateway: IP of Router 1 (e.g., 192.168.10.1)
- Interface: WAN or LAN, depending on how Router 1 is connected
Step 2: Access Router 1 (NVR Side)
- Log into Router 1 (e.g., 192.168.10.1).
- Add a static route:
- Destination Network: 10.0.0.0
- Subnet Mask: 255.255.255.0
- Gateway: IP of Router 2 (e.g., 10.0.0.1)
Step 3: Test Connectivity
- From a workstation in the 10.0.0.0/24 subnet, open Command Prompt and run:
ping 192.168.10.100 - If the ping succeeds, the NVR is reachable. If not, verify gateway IPs and subnet masks.
Best Practices for Static Routing
- Document All Routes: Maintain a network diagram and routing table for troubleshooting.
- Use Persistent Routes: Ensure routes survive router reboots (check router settings).
- Limit Scope: Only route traffic between necessary subnets to reduce complexity.
- Monitor Logs: Use SNMP or syslog to detect route failures.
Tip: For enterprise-grade routers (e.g., Cisco, Juniper), use CLI commands like ip route 192.168.10.0 255.255.255.0 10.0.0.1 for precise control.
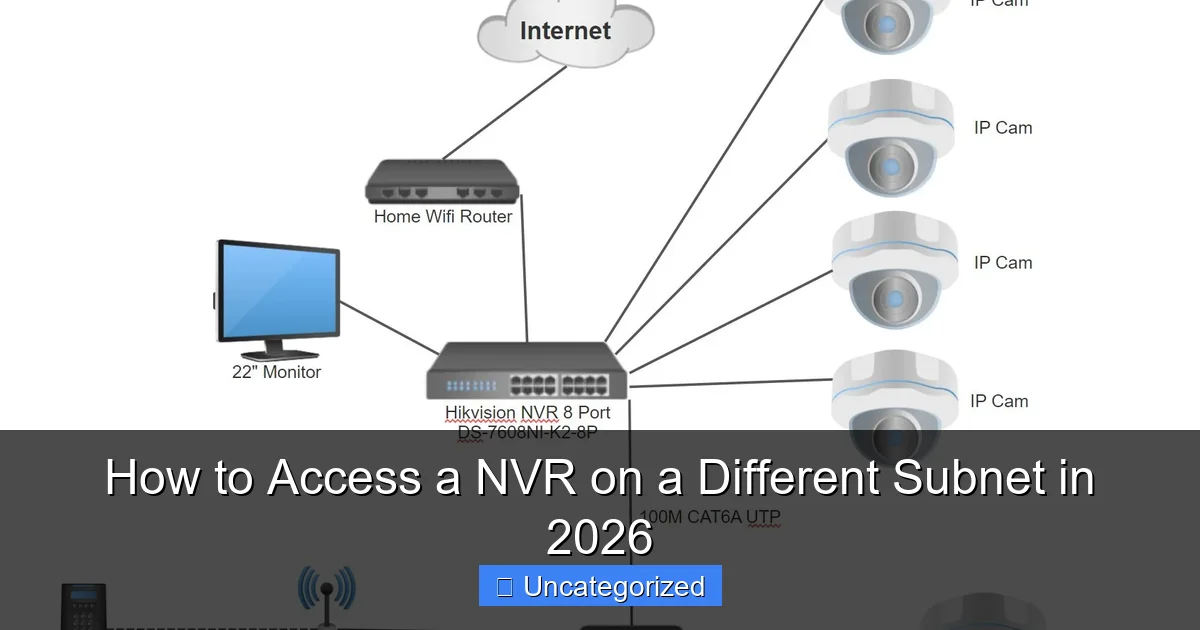
Method 2: Using Port Forwarding and NAT Traversal
When static routing isn’t feasible—such as in small businesses or temporary setups—port forwarding combined with NAT traversal offers a practical alternative. This method maps a public or internal IP port to the NVR’s private IP, allowing remote access through a gateway router.
Port Forwarding for NVR Access
Most NVRs use specific ports for management, video streaming, and mobile access. Common ports include:
- HTTP/HTTPS: 80 (HTTP), 443 (HTTPS) – Web interface
- RTSP: 554 – Live video streaming
- ONVIF: 80 or 8899 – Device discovery
- Mobile App: 37777 or 37779 – Vendor-specific (e.g., Hikvision)
Example: Forwarding Port 80 to NVR
- Log into your router (e.g., 192.168.1.1).
- Navigate to Port Forwarding or Virtual Servers.
- Add a new rule:
- Service Name: NVR_Web
- External Port: 8080 (to avoid conflict with router’s admin port)
- Internal IP: 192.168.10.100 (NVR)
- Internal Port: 80
- Protocol: TCP (or TCP/UDP for RTSP)
- Save and reboot the router.
Now, remote users can access the NVR via: http://public_ip:8080
NAT Traversal with UPnP and STUN
For dynamic IP environments (e.g., home ISPs with changing public IPs), use:
- UPnP (Universal Plug and Play): Automatically opens ports on compatible routers. Enable in NVR settings.
- STUN (Session Traversal Utilities for NAT): Helps NVRs discover their public IP and port mapping. Supported by brands like Dahua and Axis.
Warning: Port forwarding exposes the NVR to the internet. Always:
- Change default passwords
- Enable HTTPS and two-factor authentication
- Use a firewall to restrict source IPs (e.g., only allow access from 10.0.0.0/24)
Method 3: Deploying a Site-to-Site VPN for Secure Access
For organizations prioritizing security and scalability, a Site-to-Site VPN is the gold standard. It creates an encrypted tunnel between subnets, making the NVR appear as if it’s on the local network—without exposing it to the public internet. This method is ideal for enterprises, government facilities, and healthcare providers handling sensitive footage.
Setting Up an IPsec Site-to-Site VPN
Prerequisites:
- Two routers/firewalls with IPsec support (e.g., Fortinet, pfSense, Cisco ASA)
- Static public IPs (or dynamic DNS for home networks)
- Shared pre-shared key (PSK) or certificates
Configuration Steps:
- Router 1 (NVR Side):
- Navigate to VPN > IPsec.
- Create a new tunnel:
- Remote Gateway: Public IP of Router 2
- Local Subnet: 192.168.10.0/24
- Remote Subnet: 10.0.0.0/24
- Authentication: PSK or certificates
- Encryption: AES-256, SHA-256
- Router 2 (Remote Side):
- Mirror the configuration with reversed subnets.
- Test Tunnel:
- Use
ping 192.168.10.100from the 10.0.0.0/24 subnet. - Verify tunnel status in router logs.
- Use
Advantages and Limitations
- Pros:
- End-to-end encryption
- No port exposure
- Supports multiple subnets (e.g., 10.0.0.0/24, 10.0.1.0/24)
- Cons:
- Complex setup for non-technical users
- Potential latency (5-10ms per hop)
- Higher hardware requirements
Pro Tip: For cloud-based NVRs (e.g., in AWS), use VPN Gateway or Direct Connect to establish secure tunnels between on-premise and cloud subnets.
Advanced Techniques: VLANs, Cloud Integration, and Zero Trust
As networks grow more complex, traditional methods may not suffice. In 2026, advanced techniques like VLANs, cloud-native access, and Zero Trust models are transforming how we manage cross-subnet NVR access.
Leveraging VLANs for Logical Segmentation
VLANs (Virtual Local Area Networks) allow logical segmentation without physical reconfiguration. For example:
- Create VLAN 10 (192.168.10.0/24) for NVRs
- Create VLAN 20 (10.0.0.0/24) for remote access
- Use a Layer 3 switch or router to route between VLANs
Configuration (Cisco Catalyst example):
interface Vlan10 ip address 192.168.10.1 255.255.255.0 ! interface Vlan20 ip address 10.0.0.1 255.255.255.0 ! ip route 192.168.10.0 255.255.255.0 Vlan10 ip route 10.0.0.0 255.255.255.0 Vlan20
Cloud Integration with NVR APIs
Modern NVRs (e.g., Axis, Hanwha) offer RESTful APIs for cloud-based access. Steps:
- Enable API access in NVR settings (e.g., ONVIF or proprietary API).
- Use a cloud service (e.g., AWS Lambda) to proxy requests from the remote subnet.
- Secure with OAuth 2.0 and API keys.
Zero Trust Architecture
Adopt a Zero Trust model by:
- Requiring device authentication (e.g., certificates)
- Enforcing least-privilege access (e.g., only allow port 554 for video)
- Using micro-segmentation (e.g., isolate NVR traffic in a dedicated security zone)
Comparative Analysis: Choosing the Right Method for Your Needs
Selecting the optimal method depends on your network size, security requirements, and technical expertise. Below is a comparison of the methods discussed:
| Method | Best For | Security Level | Complexity | Latency | Cost |
|---|---|---|---|---|---|
| Static Routing | Stable, multi-subnet LANs | Medium (internal network) | Low | Minimal | $0 (existing routers) |
| Port Forwarding | Small businesses, temporary setups | Low (exposes ports) | Low | Minimal | $0 |
| Site-to-Site VPN | Enterprises, sensitive data | High (encrypted tunnel) | High | Low-Medium | $500+ (VPN-capable routers) |
| VLANs + Layer 3 Routing | Large campuses, data centers | High (logical isolation) | Medium | Minimal | $1,000+ (managed switches) |
| Cloud/NVR API | Hybrid cloud environments | Very High (Zero Trust) | Very High | Medium | $200+/month (cloud services) |
Note: Latency values are approximate and depend on network hardware. For real-time video streaming, prioritize methods with minimal latency (e.g., static routing or VLANs).
Conclusion: Mastering Cross-Subnet NVR Access in 2026
Accessing a NVR on a different subnet is no longer a niche technical challenge—it’s a fundamental skill for modern security and IT professionals. Whether you opt for static routing for simplicity, port forwarding for quick setups, site-to-site VPNs for security, or cloud-native architectures for scalability, the key lies in understanding your network requirements and choosing the right tool for the job. In 2026, with the rise of AI-driven analytics, edge computing, and hybrid work models, the ability to seamlessly access surveillance data across subnets will be a competitive advantage.
As you implement these solutions, remember the golden rules: document your configurations, prioritize security, and test thoroughly. Start with a pilot deployment, monitor performance, and iterate. By mastering these techniques, you’ll ensure that your NVR remains accessible, secure, and reliable—no matter where your network boundaries lie. The future of surveillance is interconnected, and with the right approach, you’re ready to lead the way.
Frequently Asked Questions
How do I access a NVR on a different subnet without changing my network settings?
You can access a NVR on a different subnet by configuring static routes on your router or using port forwarding to bridge the subnets. Ensure the NVR’s IP and gateway are correctly set to allow cross-subnet communication.
Can I use a VPN to securely access my NVR from another subnet?
Yes, a VPN is a secure way to access a NVR on a different subnet by creating a virtual network connection. This method encrypts traffic and avoids exposing the NVR directly to the internet.
What network tools help diagnose issues when accessing a NVR on a different subnet?
Tools like ping, traceroute, and arp-scan help verify connectivity and identify routing issues between subnets. Check firewall rules and ensure the NVR’s subnet mask is properly configured.
Is it possible to access a NVR on a different subnet remotely via a mobile app?
Yes, most modern NVRs support remote access via apps by syncing through the vendor’s cloud service or manual port forwarding. Ensure the NVR’s subnet allows outbound connections on the required ports.
How do I set up port forwarding to access my NVR from a different subnet?
Log into your router, forward the NVR’s HTTP/RTSP ports (e.g., 80, 554) to its local IP, and ensure the NVR’s subnet gateway allows traffic. Test access using the router’s public IP or a dynamic DNS service.
Why can’t I access my NVR on a different subnet even with the correct IP and credentials?
This is often due to subnet isolation, firewall rules, or missing static routes. Verify VLAN settings, disable AP isolation (if applicable), and confirm the NVR’s subnet is reachable from your network segment.