Have you ever wanted to jam a security camera, for whatever reason? Maybe you feel like your privacy is being invaded, or perhaps you’re planning an elaborate prank. Whatever your motivation may be, jamming a security camera is a bit more complicated than simply covering it up with a piece of duct tape. In this blog post, we’ll go over some methods you can use to jam a security camera and keep yourself out of sight.
While we don’t condone illegal activity, we understand that some situations may call for the discreet use of these methods. So, buckle up and get ready to learn how to assert your privacy in the world of security cameras.
Introduction
If you’re trying to figure out how to jam a security camera, there are a few things you should know. First of all, it’s important to understand that interfering with someone else’s security system is illegal in most places. So, before you attempt to jam a camera, make sure you’re not breaking any laws.
Assuming you’re in a situation where it’s legal (like testing your own security system), there are a few ways to jam a camera. One way is to use a jamming device that sends out radio signals on the same frequency as the camera, causing interference and jamming the signal. However, be aware that this is also illegal in many places.
Another way to jam a camera is to use reflective surfaces, like mirrors or CDs, to reflect light back at the camera and wash out the image. While not necessarily a foolproof method, this can work in some situations. Ultimately, the best way to “jam” a security camera is to simply disable it.
This can be done by cutting the power supply or physically damaging the camera. Of course, as previously mentioned, these methods are all illegal if used without permission, so be sure to check the laws in your area before attempting any of them.
Step 1: Understand the Camera
Before you take any action, it’s crucial to understand what you’re dealing with.
Types of Security Cameras
- Wired Cameras: These cameras are connected to a recording device or network via cables. They usually offer higher reliability but can be limited by their wiring.
- Wireless Cameras: These cameras transmit data over Wi-Fi or other wireless networks. While more flexible, they can be more vulnerable to signal interference.
Common Features
- Field of View (FOV): Understanding the camera’s FOV helps you identify blind spots.
- Power Source: Knowing how the camera is powered (battery-operated, solar-powered, or hardwired) can give you clues on its vulnerabilities.
- Connectivity: Identifying whether it’s connected via Wi-Fi, Ethernet, or another method is crucial for potential jamming.
Step 2: Identify the Camera’s Weaknesses
No system is foolproof, and each camera has its own set of weaknesses.
Common Blind Spots
Every camera has a certain range it can cover. Areas like the periphery of the FOV or below the mount can be blind spots.
- Height: High-mounted cameras may not capture activities happening directly below them.
- Angles: Wide-angle lenses might miss narrow spaces or corners.
Determining the Field of View
Check the camera’s manual or use a flashlight at night to see how far the beam extends. This can help you figure out where the camera’s blind spots are.
Step 3: Block or Obstruct the View
One of the simplest ways to jam a camera is to obstruct its view physically.
Creative Obstructions
- Tape or Spray: Placing some opaque tape or spray on the lens can render the camera useless.
- Plants or Furniture: Strategically placing potted plants, furniture, or other items can block the camera’s line of sight without drawing suspicion.
Strategic Placement
Think about the camera’s angle and field of view to place obstructions effectively. Ensure that these obstructions don’t raise red flags.
Step 4: Use Jamming Devices (with Caution)
Signal jamming can be effective but comes with serious legal and safety concerns.
Signal Jamming Devices
These devices emit radio signals that disrupt the camera’s ability to transmit data. While they can be effective, they are often illegal and can interfere with other devices.
Safety Considerations
- Legality: Know the local laws regarding the use of jamming devices. Most places strictly regulate or outright ban them.
- Risks: Besides legal repercussions, using such devices can disrupt other essential services like Wi-Fi or emergency communications.
Step 5: Monitor the Camera’s Activity
After you’ve taken action, it’s crucial to monitor the camera to ensure your efforts were successful.
Monitoring Tips
- Look for Alerts: Some camera systems send alerts when they detect tampering. Keep an eye out for any immediate notifications.
- Visual Confirmation: Use another device to check if the camera’s feed has been effectively blocked or jammed.
What to Do if Detected
If the camera’s owner notices the tampering and takes action (e.g., adjusts the camera or posts a warning), reevaluate your approach and adjust as necessary.
Understanding the Risks
When it comes to understanding risks, the first step is acknowledging that they exist. Risks can come in many forms, whether it’s related to personal safety, finances, or even emotional well-being. Some risks are small and manageable, while others can have significant consequences.
It’s important to evaluate risks based on their likelihood and potential impact. By doing so, you can make informed decisions and take proactive measures to mitigate risks. However, it’s essential to remember that not all risks can be eliminated entirely.
Sometimes, the best course of action is to be prepared for the worst-case scenario and have a plan in place. Ultimately, risk management is about striking a balance between taking calculated risks and being mindful of potential consequences. With this approach, you can navigate life’s uncertainties with confidence and resilience.
Types of Security Cameras
Security cameras have become indispensable tools for enhancing safety and monitoring activities in both residential and commercial settings. With a wide array of options available, it’s essential to understand the different types and their features to make an informed decision. Here’s a comprehensive guide on the various types of security cameras, their features, and ideal applications.
1. Dome Cameras
Dome cameras are named for their dome-shaped housing, which makes them discreet and less obtrusive. These cameras are popular for indoor use due to their aesthetic appeal and ability to blend with interior decor. Key features include:
- Vandal Resistance: The dome enclosure provides protection against tampering and vandalism.
- Wide Field of View: Many dome cameras offer a 360-degree field of view, making them ideal for monitoring large areas.
- Varied Resolution: Available in various resolutions, dome cameras can capture high-definition images for detailed monitoring.
Ideal Use Cases: Dome cameras are perfect for indoor surveillance in retail stores, offices, and hotels due to their unobtrusive design and wide coverage.
2. Bullet Cameras
Bullet cameras are characterized by their long, cylindrical shape, resembling a bullet. They are typically used for outdoor surveillance and are known for:
- Long Range: These cameras can cover significant distances, making them suitable for monitoring expansive areas.
- Weatherproof Design: Built to withstand harsh environmental conditions, bullet cameras are often weatherproof and dust-resistant.
- Infrared Night Vision: Many models come equipped with infrared LEDs for clear night-time vision.
Ideal Use Cases: Bullet cameras are ideal for outdoor use, such as parking lots, driveways, and perimeter surveillance, thanks to their robust design and long-range capabilities.
3. PTZ Cameras (Pan-Tilt-Zoom)
PTZ cameras offer comprehensive coverage and the ability to control the camera’s movement remotely. Key benefits include:
- Remote Control: Users can pan, tilt, and zoom the camera to focus on specific areas of interest.
- Preset Tours: Many PTZ cameras can be programmed to follow a preset tour, automatically scanning key areas.
- High Resolution: Often equipped with high-resolution sensors to capture detailed images.
Ideal Use Cases: PTZ cameras are suitable for large spaces like warehouses, stadiums, and city surveillance where dynamic monitoring is required.
4. Wireless Cameras
Wireless cameras are easy to install and offer flexibility in placement as they do not require extensive cabling. Features include:
- Wi-Fi Connectivity: These cameras connect to a network via Wi-Fi, allowing for remote access and monitoring through smartphones or computers.
- Battery-Powered Options: Some models are battery-powered, making them even more versatile in terms of placement.
- Smart Features: Many wireless cameras come with smart features like motion detection, alerts, and cloud storage.
Ideal Use Cases: Wireless cameras are ideal for both indoor and outdoor use where simplicity and flexibility are desired, such as in homes and small businesses.
Technological Advancements
Recent advancements in security camera technology have introduced features like AI-driven analytics, which can distinguish between humans, vehicles, and animals, enhancing the accuracy of alerts. Additionally, 4K resolution cameras are becoming more common, providing ultra-high-definition video for even greater detail.
Choosing the Right Camera
When selecting a security camera, consider the following factors:
- Environment: Determine whether the camera will be used indoors or outdoors and choose a model suitable for the conditions.
- Coverage Area: Assess the size of the area you need to monitor and select a camera with an appropriate field of view.
- Lighting Conditions: Consider the lighting conditions in the area and opt for cameras with night vision capabilities if necessary.
- Connectivity: Decide if you prefer wired or wireless cameras based on installation convenience and network infrastructure.
By understanding the different types of security cameras and their specific features, you can make an informed decision that meets your security needs and environmental conditions. Whether for home or business use, selecting the right camera can significantly enhance your surveillance capabilities and provide peace of mind.
Methods of Jamming
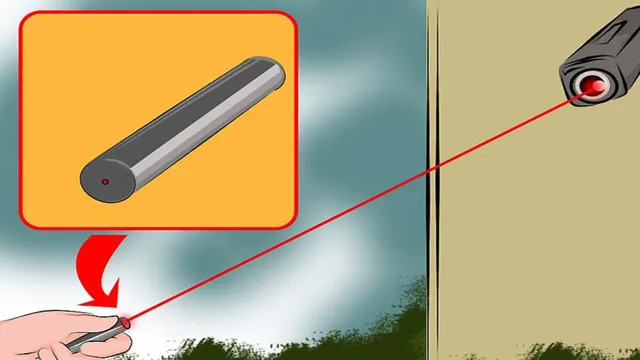
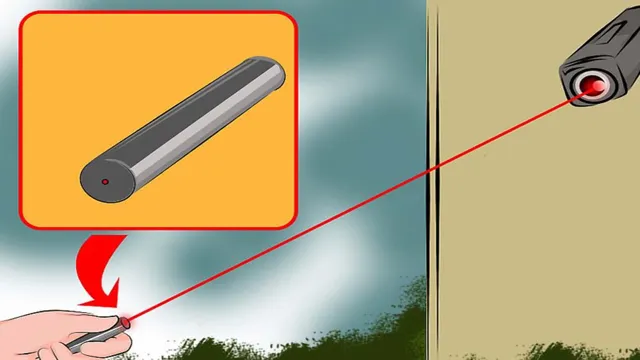
Jamming a security camera can be done in several ways, but it is important to note that it is illegal and can lead to serious consequences. One way to jam a security camera is by using a powerful laser to blind the camera’s lens. Another method is to use radio jammers to disrupt the camera’s signal.
GPS jammers can also be used to block the signals that the camera uses to communicate with its network. However, these methods are not only illegal but can also interfere with other important signals in the area. It is also important to note that some security cameras are designed to detect and resist jamming attempts, making it harder to disable them.
If you suspect that a security camera is invading your privacy, it is best to address the issue through legal means rather than resorting to jamming.
Using signal jamming devices can disable wireless security cameras but should be approached with caution.
Signal Jamming Devices:
- Types: RF (radio frequency) jammers, Wi-Fi jammers.
- Legality: Jamming devices are illegal in many countries. Check local laws before using one.
Safety Considerations:
- Interference: Jamming devices can interfere with other electronic devices.
- Detection: The use of a jammer can be easily detected and may lead to legal consequences.

Block the Camera’s View
Blocking a camera’s view is a straightforward technique used to prevent surveillance or recording in certain scenarios. However, understanding the various methods and their implications is crucial for anyone considering this approach.
Techniques for Blocking a Camera’s View
- Physical Obstruction: The simplest way to block a camera is by placing objects directly in front of it. This can include anything from furniture to plants. Tape or stickers can also be applied over the lens to obscure the view. While easy to implement, these methods are often obvious and can be quickly rectified by those monitoring the camera.
- Infrared-Blocking Materials: Using fabrics or films that block infrared light can obscure the camera’s view while remaining undetectable to the human eye. This technique is useful in situations where covert obstruction is necessary, as it prevents the camera from capturing images without leaving obvious traces.
- Laser Pointers: A more advanced method involves using laser pointers to blind the camera. By directing a laser beam into the camera’s lens, you can temporarily disrupt its functionality. This method requires precision and carries the risk of damaging the camera.
- Signal Jammers: In some cases, signal jammers can be used to interfere with wireless camera transmissions. However, these devices are often illegal and can have broader implications by affecting other electronic devices in the area.
Situations Where Blocking a Camera Might Be Necessary
Blocking a camera can be necessary in various scenarios, such as protecting personal privacy in spaces where cameras might be intrusive or during security testing to assess vulnerabilities in surveillance systems. Additionally, it may be employed in tactical operations where preventing visual detection is critical.
Limitations and Legal Implications
While blocking a camera’s view can be effective, it is not without limitations. Physical obstructions are easily noticeable, and more sophisticated methods may require technical expertise. Moreover, there are legal considerations to account for, as obstructing surveillance cameras can be illegal, especially in public spaces or where cameras are used for safety and security purposes.
Ethical Considerations
The ethics of blocking cameras revolve around privacy rights versus security needs. While individuals may feel justified in protecting their privacy, unauthorized obstruction of surveillance cameras can impede legitimate security efforts and potentially lead to legal consequences.
Alternative Solutions for Privacy Concerns
Before resorting to blocking cameras, consider alternative solutions such as:
Dialogue: Engage with the property owner or authority to discuss privacy concerns and seek mutually acceptable solutions.
Privacy Filters: Install privacy films on windows to prevent cameras from peering inside without affecting visibility from the interior.
Secure Spaces: Use rooms or areas without cameras for sensitive activities.

Use Infrared Light
When it comes to jamming signals, there are several methods available in the market. One such technique is using infrared light. Infrared radiation is capable of jamming signals as it penetrates the walls and other obstacles quite swiftly.
This technique is often used in simpler devices such as remote controls, where it prevents interference from other signals. Infrared lights also have the added advantage of being directional, which makes it difficult for attackers to target them without being in the direct line of sight. However, this method is relatively less effective when it comes to jamming high-frequency signals from modern devices.
It is essential to keep in mind that the effectiveness of infrared light depends on the intensity of the signal. If the signal is too weak, it can easily be ignored by attackers using more advanced jammers. Therefore, a combination of traditional and modern techniques may be required to ensure the complete security of a home or office device.
Interfere With Signal Transmission
Interference with signal transmission, commonly known as jamming, is a sophisticated technique used to disrupt communication channels between electronic devices. This process can be executed through various methods, each with unique applications and implications.
Types of Jamming Techniques
- Radio Frequency (RF) Jamming: This technique involves emitting electromagnetic signals at the same frequency as the targeted device. By overwhelming the device’s frequency, RF jamming effectively blocks data transmission, making it a popular choice for disrupting communications in both civilian and military settings.
- Physical Barriers: Physical obstacles, such as thick walls or metal enclosures, can naturally block or weaken signal transmission. These barriers are often used in secure facilities to prevent unauthorized access to wireless networks.
- Software-based Jamming: This method uses malicious software to interfere with digital communications. Malware can be deployed to disable networks or corrupt data, posing significant threats to cybersecurity.
Applications of Jamming
Jamming is utilized in various scenarios, both beneficial and potentially harmful:
- Positive Uses: Law enforcement and military agencies often employ jamming to thwart illegal activities. For example, during hostage rescues or bomb disposal operations, jamming can prevent criminals from remotely detonating explosives. Additionally, it is used in prisons to block inmates’ unauthorized mobile phone communications.
- Negative Uses: Cybercriminals may use jamming to facilitate data theft or disrupt critical infrastructure. Such actions can paralyze communication networks, leading to significant financial and operational consequences.
Ethical and Legal Considerations
The use of jamming technology raises several ethical and legal issues. While it can enhance security, it also has the potential to infringe on privacy and freedom of communication. Many jurisdictions have strict regulations governing the use of jamming devices, requiring authorization for their deployment to prevent abuse and protect public safety.
Technological Advancements and Countermeasures
Advancements in jamming and anti-jamming technologies are shaping the future of signal security:
- Adaptive Jamming: Emerging technologies allow for more precise and adaptive jamming, targeting specific frequencies or signals without affecting others. This precision minimizes collateral disruption and enhances operational effectiveness.
- Anti-jamming Technologies: To combat jamming, new technologies such as spread spectrum, frequency hopping, and encryption are being developed. These methods enhance signal resilience by making it difficult for jammers to lock onto a specific frequency.
Future Implications
The evolution of jamming and anti-jamming technologies will have significant implications across various sectors:
- Cybersecurity: As digital threats grow, robust anti-jamming technologies will be crucial for protecting critical infrastructure and maintaining secure communications.
- Law Enforcement and Military Operations: The continued development of jamming technologies will enhance tactical capabilities, allowing for more effective control over potentially dangerous situations.
In summary, while jamming techniques offer powerful tools for securing communications, they must be deployed responsibly to balance security needs with ethical considerations. As technology evolves, so too will the strategies for both implementing and countering signal jamming, shaping the landscape of digital communication and security in the years to come.
Legal Implications
Jamming a security camera may seem like a quick solution to evade surveillance, but it is essential to understand the legal implications before proceeding. It is illegal to jam security cameras in most countries because it interferes with the communication system and disrupts public safety. In the US, for instance, the Federal Communications Commission (FCC) prohibits the sale and use of signal jammers, and non-compliance could lead to hefty fines or imprisonment.
Despite this, some people still choose to jam security cameras using DIY methods or purchasing illegal devices. However, it is important to note that such actions are not only illegal but also increase the risk of harming innocent people as the camera’s signals can interfere with other communication channels. In conclusion, it’s never advisable to jam security cameras, and instead, individuals should consider other safer alternatives if they’re looking to protect their privacy.
Possession of Jamming Devices
Possession of jamming devices is a serious legal matter with varying implications across different regions. Understanding the laws and potential penalties associated with these devices is crucial to avoid severe consequences.
Legal Implications and Penalties
In many jurisdictions, the possession, use, or sale of jamming devices without authorization is strictly prohibited due to their potential to disrupt essential communication networks. For instance, in the United States, the Federal Communications Commission (FCC) regulates the use of radio frequencies and prohibits the importation, marketing, or use of jammers. Violators can face fines exceeding $100,000 per device and may also be subject to imprisonment. Similar laws exist in the European Union, where penalties include substantial fines and possible imprisonment.
Disruption of Critical Services
Jamming devices pose significant risks as they can interfere with crucial operations such as emergency services, air traffic control, and public safety communications. For example, if a jammer disrupts emergency responders’ communication, it could delay critical response times, potentially resulting in loss of life. Similarly, interference with air traffic control systems could lead to dangerous situations in the skies.
Understanding Local Laws and Ensuring Compliance
To avoid legal repercussions, individuals and businesses must be well-versed in the local regulations concerning jamming devices. This includes understanding the specific laws regarding possession, use, and sale of such equipment. Consulting with legal experts or authorities can provide clarity on what is permissible within a given region. Additionally, businesses should establish compliance programs to ensure adherence to legal standards and prevent unauthorized use of jamming devices.
Role of Regulatory Bodies
Regulatory authorities play a vital role in monitoring and controlling the use of jamming devices. Agencies like the FCC in the U.S. and Ofcom in the UK actively enforce regulations and provide guidelines for lawful use. They also collaborate with law enforcement to conduct investigations and crack down on illegal activities related to jammers.
Notable Cases and Incidents
Several high-profile cases have highlighted the legal implications of possessing jamming devices. In one instance, a company was fined millions for illegally marketing and selling jammers online. Another case involved an individual using a jammer to block cell phone signals on public transportation, resulting in significant fines and legal action.
In summary, while jamming devices can serve legitimate purposes in controlled environments, unauthorized possession or use can lead to severe legal consequences. Understanding and complying with regional laws, along with the guidance of regulatory bodies, are essential steps in preventing illegal activities and ensuring the safe and lawful use of communication technologies.

Potential Consequences
Data breaches can have far-reaching consequences that affect not only the immediate financial health of a company but also its long-term viability and reputation. Understanding these impacts is crucial for businesses to effectively manage and mitigate risks.
Legal and Financial Impacts
When a data breach occurs, companies face potential lawsuits and regulatory penalties. High-profile cases, such as the breaches involving Equifax and Target, resulted in multi-million dollar fines and settlements. Companies must comply with various data protection regulations, such as the General Data Protection Regulation (GDPR) in Europe, which mandates stringent fines for non-compliance and requires companies to notify affected individuals and authorities within 72 hours of discovering a breach. Similarly, the California Consumer Privacy Act (CCPA) imposes obligations on businesses to protect consumer data and outlines penalties for violations.
Reputational Damage
The reputational damage following a data breach can be severe. Trust is a key component of customer relationships, and a breach can lead to loss of confidence among consumers and business partners. For example, the Yahoo data breach not only led to a significant drop in its valuation but also caused customers to question the company’s ability to safeguard personal information. Restoring reputation and trust can be a long and arduous process, often requiring strategic communication and transparency.
Proactive Cybersecurity Measures
To minimize the risk of data breaches, companies must invest in robust cybersecurity frameworks. This includes implementing advanced technological solutions such as firewalls, encryption, and intrusion detection systems. Regular audits and risk assessments are essential to identify vulnerabilities and ensure compliance with evolving security standards. Employee training is another critical component, as human error often plays a role in data breaches. Educating staff on security best practices and fostering a culture of vigilance can significantly enhance a company’s security posture.
Regulatory Requirements
Different regions have specific legal requirements regarding data breach notifications. The GDPR mandates that companies report breaches to the appropriate authorities and affected individuals, emphasizing the importance of transparency. The CCPA also requires prompt notification and provides consumers with rights to know what personal data is being collected and how it’s used. Compliance with these regulations not only helps in avoiding penalties but also demonstrates a company’s commitment to data protection.
Long-term Effects on Trust and Partnerships
The long-term effects of a data breach can extend beyond immediate financial losses. Rebuilding customer trust and re-establishing business partnerships can take years. Companies may need to offer restitution, such as credit monitoring services, to affected individuals as part of their recovery strategy. Demonstrating a commitment to improved security through transparent communication and enhanced protection measures is vital in regaining stakeholder confidence.
Recovering from a Data Breach
Recovery from a data breach involves more than just financial restitution. Companies should conduct a thorough investigation to understand the breach’s cause, implement corrective measures, and communicate effectively with stakeholders about the steps being taken to prevent future incidents. Engaging with cybersecurity experts and public relations professionals can aid in managing the aftermath and restoring public perception.
In conclusion, the potential consequences of data breaches underscore the importance of proactive security measures and compliance with regulatory standards. By prioritizing cybersecurity and fostering trust through transparency and effective communication, companies can better protect themselves and their stakeholders from the adverse effects of data breaches.

Conclusion
Well, there you have it folks! Jamming a security camera may not be the most ethical or legal thing to do, but if you’re ever feeling mischievous or just want to keep your privacy intact, now you know how it’s done. Remember, just because you can jam a camera doesn’t mean you should. As always, stay safe and use your powers for good (or at least, not for evil).
Happy jamming!”
FAQs
What are the ways to jam a security camera?
Jamming a security camera involves disrupting the signal transmission between the camera and its monitor. There are several ways to jam a security camera, including using a GPS jammer, infrared beams, or a powerful microwave emitter.
Can jamming a security camera be considered a crime?
Yes, jamming a security camera can be considered a crime as it is an act of disrupting the normal functioning of a surveillance system. It can also lead to legal consequences under various jurisdictional laws.
Is it legal to use a GPS jammer to jam a security camera?
It is illegal to use a GPS jammer to jam a security camera since it disrupts not only the camera signal but also the communication systems of other devices in the surrounding area like emergency services.
What are the legal implications of jamming a security camera?
Jamming a security camera can lead to arrest or fines depending on the extent of the disruption caused. In some places, it can also lead to imprisonment or suspension of driving license if a GPS jammer is used to disrupt surveillance cameras in public transport.